Share this post
Authentication
Authentication is the process of verifying a user’s identity to ensure they are who they claim to be before granting access to secure systems.
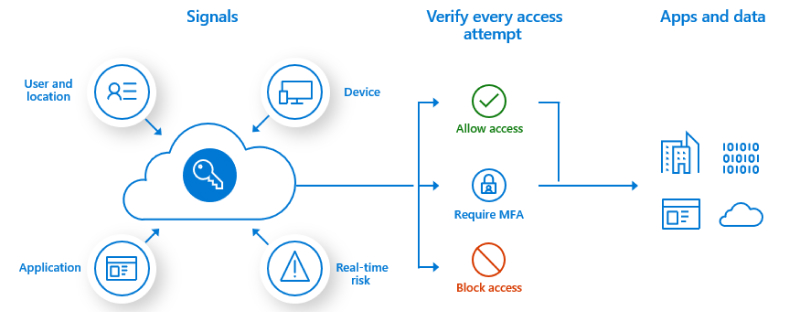
Authentication is essential in digital security, serving as the gatekeeper that determines whether a user can access certain resources. Whether you’re logging into a social media account or accessing sensitive corporate data, authentication is the first step in the security process.
Traditionally, authentication relies on passwords—something only the user knows. However, passwords alone can be vulnerable to attacks such as phishing or brute force. To address this, multi-factor authentication (MFA) has become more widespread. MFA combines something you know (like a password) with something you have (a smartphone or token) or something you are (biometrics, like a fingerprint). This layered approach significantly enhances security by making it more difficult for unauthorized users to gain access.
In addition to security, authentication also plays a crucial role in user experience. For instance, biometric authentication, like facial recognition, allows for quick and seamless access to systems, enhancing convenience without compromising security.
However, authentication isn’t without its challenges. Users often struggle with password fatigue—remembering multiple complex passwords across various platforms. This is where tools like password managers and innovations like single sign-on (SSO) come into play, simplifying the authentication process while maintaining strong security protocols.
Looking to the future, advancements in artificial intelligence and machine learning are paving the way for continuous authentication methods. These systems monitor user behavior in real-time, ensuring that the person accessing the system is continuously authenticated throughout their session.
In summary, authentication is a critical component of digital security, evolving from simple password-based systems to more sophisticated multi-factor and biometric methods. Its effectiveness is vital for protecting sensitive information, enhancing user experience, and meeting regulatory compliance.

